Wednesday, 1 January 2020
Creating an ALB from the AWS CLI
In this article, we will create an application load balancer from the command line interface.
**Scenario:**
We would have an ALB serving a single point of contact for clients with two listeners forwarding traffic to target groups with health check.
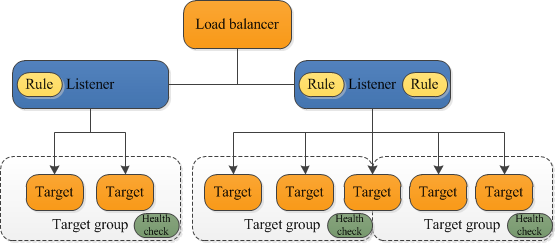
**Prerequisites:**
- awscli has been installed
- two EC2 instances are configured
- instance 1:
- default VPC
- subnet: us-east-1a
- auto-assign public IP: enable
- instance 2:
- default VPC
- subnet: us-east-1b
- auto-assign public IP: enable
First, login in to the admin instance using ssh
```bash
ssh @
```
Once you are in, configure your aws settings.
```bash
aws configure
```
Fill in the following values:
```
AWS Access Key ID [None]:
AWS Secret Access Key [None]:
Default region name [None]: us-east-1
Default output format [None]:
```
Supposing your instances are in default VPC
```bash
aws ec2 describe-vpcs --filters "Name=isDefault, Values=true"
```
Once you get the ID of VPC, use the follwoing command to get subnet IDs:
```bash
aws ec2 describe-subnets --filters "Name=vpc-id,Values=" --query 'Subnets[*].{ID:SubnetId}'
```
To get security group ID:
aws ec2 describe-security-groups --filter Name=vpc-id,Values= Name=group-name,Values=
Then enter the following command and replace and
```bash
aws elbv2 create-load-balancer --name alblab-load-balancer --subnets --security-groups
```
An ALB is created. The next step is to create a target group.
```bash
aws elbv2 create-target-group --name demo-targets --protocol HTTP --port 80 --vpc-id
```
Copy ``TargetGroupArn`` which will be used later
Then, register the targets
```bash
aws elbv2 register-targets --target-group-arn --targets Id= Id=
```
For the instance IDs, you can use ``aws ec2 describe-instances`` to get them.
Then, enter the following command to create a listener:
```bash
aws elbv2 create-listener --load-balancer-arn --protocol HTTP --port 80 --default-actions Type=forward TargetGroupArn=
```
Perform a health check with the following command:
```bash
aws elbv2 describe-target-health --target-group-arn
```
At this moment, the status of the instances is unhealthy. It is because we still need to configure out instances as web servers.
Log in to instance 1 using ssh and run the following commands:
```bash
sudo yum update -y
sudo yum install -y httpd
sudo service httpd start
sudo chkconfig httpd on
```
If you copy the public IP address and paste it into a browser. You should see the Apache test page. If not, that means your ingress on the instance's security group is incorrect. It should allow HTTP on port 80.
If you copy the DNS name and paste it into a browser, you should see the Apache test page.
However, if we take a look at the target groups. We will see the instanecs are unhealthy. The health check for the ALB is checking the return code of 200, but currently there is no ``index.html`` page for the instances to return the 200 code to the ALB.
Let's create one.
```bash
cd /var/www/html
sudo touch index.html
sudo chmod 777 index.html
vi index.html
```
Add something to index.html
Save and exit by pressing Esc and typing
```bash
:wq
```
Then we do the same thing for instance 2.
Once you have done, go back to admin instance.
Verify the target health check
```bash
aws elbv2 describe-target-health --target-group-arn
```
You should be see "OK" message.
Subscribe to:
Post Comments (Atom)
A Fun Problem - Math
# Problem Statement JATC's math teacher always gives the class some interesting math problems so that they don't get bored. Today t...
-
SHA stands for Secure Hashing Algorithm and 2 is just a version number. SHA-2 revises the construction and the big-length of the signature f...
-
## SQRT Decomposition Square Root Decomposition is an technique optimizating common operations in time complexity O(sqrt(N)). The idea of t...
No comments:
Post a Comment